Planning & Productivity
6 MIN ARTICLE
If you don’t have a cybersecurity plan in place in your practice, you could be putting your business and clients at risk. Here’s a five-step framework to help financial advisors get started with cybersecurity.
1. Identify potential cyber threats
2. Protect from known (and unknown) cyber risks
3. Detect early signs of a security breach
4. Respond immediately with a procedure in place
Think of the average hacker as a lazy thief rattling doorknobs. If the door is locked, sure, they could break a window or look for some other way in. But they’re more likely to move on until they find someone that left their door open. Implementing even basic cybersecurity measures can help create barriers to entry for these threats and mitigate the cyber risk facing your practice and, by extension, your clients.
Why is cybersecurity important to a financial advisor’s practice? In a recent survey of over 1,000 executives across 20 countries and various industries, Deloitte found 91% of organizations reported at least one cyber incident or breach.1 If a cyberattack occurs in your business, it’s important to have a procedure in place to respond and recover quickly.
How to get started with cybersecurity
So how do you start locking doors? The National Institute of Standards and Technology (NIST), part of the U.S. Department of Commerce, publishes a cybersecurity framework for organizations wondering where to start with protecting a business.2 It includes five phases in the lifecycle of a cybersecurity policy: identify, protect, detect, respond and recover. Here’s an overview to help advisors with each step.
A five-step framework for cybersecurity
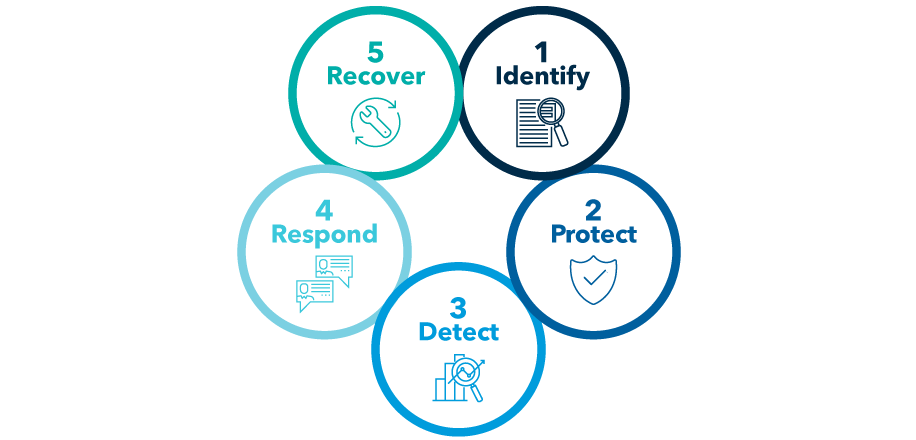
Source: NIST, 2021
1. Identify potential cyber threats
The first step in developing a better cybersecurity posture is to identify critical processes and assets. This involves taking a full inventory of both hardware and software used in your firm and the type of personal identifying information that you store and share, as well as understanding the types of threats to your business that might exist.
There are many types of threats to financial professional firms, according to the Financial Industry Regulatory Authority (FINRA). These include phishing (where employees respond to an email from an untrustworthy source and provide information or a digital connection in the process), malware (which can infect your access to data), account takeovers, fraudulent wire transfers and vendor breaches.
One of the most widespread threats currently facing advisors is ransomware, a type of malicious software that encrypts a target’s data. This data is then "held hostage," as attackers demand a payment in exchange for the decryption key. In December 2022, FINRA warned financial advisors that it had "received reports about increasing numbers and sophistication of ransomware incidents."3 Attackers have increasingly targeted small and midsize firms, warns FINRA.
These attacks can be costly. NetDiligence’s 2022 Cyber Claims Study,4 which analyzes insurance claims related to cyber incidents, found that 28.5% of the claims it reviewed between 2017 and 2021 were due to ransomware attacks. Such attacks were the leading cause of loss for small and mid-sized enterprises, with average ransoms of $262,000, rising to $8.6 million on average for larger companies.
But the cost of falling victim to an attack goes beyond whatever ransom the hacker might extract, or what secrets they might steal. Small and mid-sized businesses spent $146,000 on average for crisis services costs associated with responding to a cyberattack event, such as customer communications and public relations, according to NetDiligence. Large companies spent an average of $2.2 million coordinating responses.
Which cyberattacks are most costly?
Ransomware may lead to the largest number of claims and highest losses for small and medium-sized enterprises, but it’s not the only costly threat.
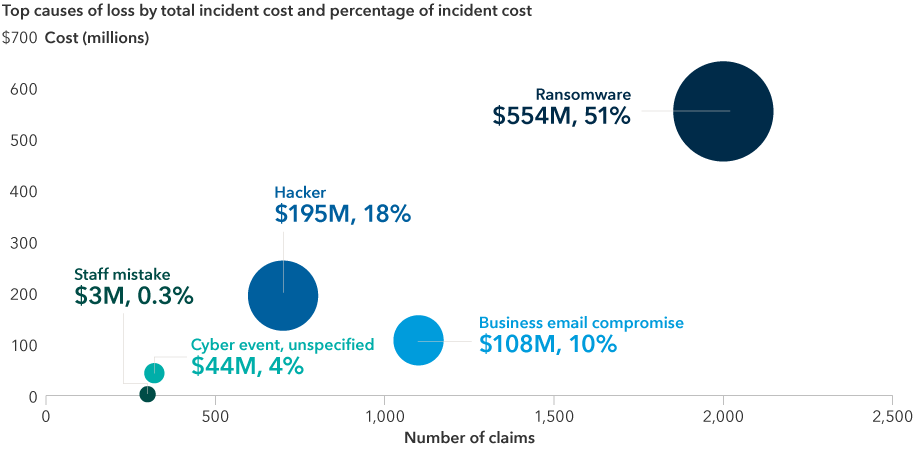
Source: NetDiligence Cyber Claims Study, 2022
2. Protect from known (and unknown) cyber risks
Once you have an inventory of your assets and key risks, it’s time to begin putting safeguards in place. Conducting regular backups of your data, for example, can help provide a crucial bulwark against ransomware.
You can also work to protect sensitive data by using encryption and managing access to devices and applications. It is highly recommended that all team members have strong, unique passwords for every account. (Password manager software can help with this.) And you may want to consider enabling multifactor authentication wherever possible.
In cybersecurity, the "principle of least privilege" means that users should only have access to the minimum resources required for their jobs. Strong passwords, multifactor authentication and education on common threats (like phishing attacks) can help prevent an account from being breached. But should a breach occur anyway, access controls can help contain the damage.
3. Detect early signs of a security breach
While robust planning and preparation are important, it’s no guarantee of safety. It’s important to stay vigilant for any signs of a breach. Defenders need to be right 100% of the time, while attackers only have to succeed once.
Regular detection involves maintaining and monitoring logs for unusual traffic. For example, a login to an important account from an unknown device merits suspicion, especially if that device appears to be located in another country.
Complicating things further, some cyber threats are beyond a firm’s immediate control. In their 2023 Threat Predictions,5 cybersecurity firm Trellix wrote: "We expect to see an increase in breaches related to supply chain issues in 2023." Citing research from IBM, Trellix wrote that 19% of all breaches are a result of supply chain issues.
"Both threat actors and security researchers are likely to heighten their study of the underlying frameworks, which are part of the supply chain," according to the Trellix report, which adds that future vulnerabilities "won’t necessarily come in the form of a major Microsoft bug, but a framework you may have never heard of that everyone is using."
4. Respond immediately with a procedure in place
When it comes to cyberattacks, there is a significant amount of underreporting of incidents. Businesses often won't publicize an attack to avoid inviting further ransom-seekers, or simply to spare themselves the embarrassment of bad press. But a head-in-the-sand approach will not serve your business or your clients. In fact, there is a way to address the incident while reinforcing a degree of confidence that there is a plan in place.
For example, having standard operating procedures (SOPs) for what happens should a cyberattack occur can provide a degree of peace of mind to internal and external stakeholders. Alternatively, FINRA offers a small-firm Cybersecurity Checklist in the form of a spreadsheet to help guide users through a third-party security review and remediation plan.
Aside from the obvious public relations considerations, a full response plan should also include legal counsel. (There are attorneys who specialize in data security and privacy.) Furthermore, consider implementing a notification procedure for impacted clients and a credit/ID monitoring plan, if applicable. Law enforcement and other relevant authorities should also be notified.
The exact response required will depend on the scope of the attack. Consider forming multiple response plans to cover different scenarios. And once you’ve formalized your plans, it’s important to test them. Communicate to everyone involved what will be expected of them in the case of a breach.
5. Recover with strong communication and lessons learned
The fifth step in NIST’s framework is to recover. This includes updating response plans with lessons learned, bringing important systems back online and clearly communicating with any and all affected parties.
If any data has been altered or lost, this is where the benefits of regular backups become apparent. Consider storing backup material for critical systems in a different location (or in "the cloud") to mitigate the additional risk of a physical event, such as extreme weather, taking out your systems and backups in one fell swoop.
A thorough forensic examination of your systems by an expert can be a good idea. Penetration testers can help you find any obvious gaps. Attackers often attempt to achieve "persistence" — the ability to get into your systems and stay there. Even if the initial breach is discovered and the attacker booted out of your network, they may have placed a hidden "backdoor" that allows them to regain access. The extent of the recovery activities will again depend on the severity of the attack.
Beyond this framework, the NIST offers additional resources for small businesses seeking to improve their cybersecurity posture. FINRA also has cybersecurity resources specifically for financial advisors, including guidance on applicable regulations and a small-business cyber checklist to walk through.
Ways to reduce future risks
There are a few other simple things firms can do to mitigate their cyber risks. Regular software updates, for example, are more important than you might think. That "remind me tomorrow" button can be tempting, but software companies push those updates out for a reason.
Sometimes those updates might be a new feature, or a change in color palette. Other times, they’re a patch for a critical vulnerability that was discovered in the code. Selecting "Accept updates" may require your machine’s attention for a few minutes but running out-of-date software can expose you and your business to needless risk.
It’s also important to avoid common misconfigurations that hackers might be known to poke around for. The vendor of any third-party software or tools you’re using should be able to talk you through how to set up a new system securely. Many vendors also host robust documentation online that can provide helpful tips and tricks.
Sharing the reality of cyber threats with employees and offering education about avoiding suspicious emails and websites can also help reduce risks. This is another area where having a clear SOP can help. Employees can learn the procedures during the onboarding process, and even be required to review them each year for updates or to reinforce best practices.
While the risks of cybersecurity are real, they should not be overwhelming. Small security steps can make a big difference. There’s no need to build a fortress. Sometimes, just locking that front door can be enough.
1 Deloitte, "Global Future of Cyber Survey," 2023.
2 National Institute of Standards and Technology, "Getting Started with the NIST Cybersecurity Framework: A Quick Start Guide," August 2021.
3 FINRA Alerts Firms to Increasing Ransomware Risks, December 2022.
4 Net Diligence, "Cyber Claims Study," 2022.
5 Trellix Advanced Research Center, "2023 Threat Predictions."
Cybersecurity checklist
Five simple steps can make any small-business owner feel more prepared.
