Marketing & Client Acquisition
Practice Management
- RIAs are not immune from the uptick in corporate cyberattacks.
- Regulators are increasingly taking notice and offering guidance on how RIAs should protect data.
- Straightforward steps can help RIAs start to lock down their businesses and help protect clients.
Bonus download: Clients need to do their part to keep their data safe, too. Download a guide that includes simple pointers to share with clients.
Hackers have two nicknames for RIAs: “low-hanging fruit” and “honeypots.”
Why? RIAs are known as easy and potentially lucrative targets for cyberattackers, says Brian Edelman, CEO of FCI, a firm that specializes in helping RIAs boost their cybersecurity. In many ways, RIAs are exactly what “bad actors” are looking for, he says. They often control large amounts of personal financial information and lack a hardened cyberdefense or strategy in many cases. RIAs are often run by independent advisors without the support of a large technology infrastructure behind them.
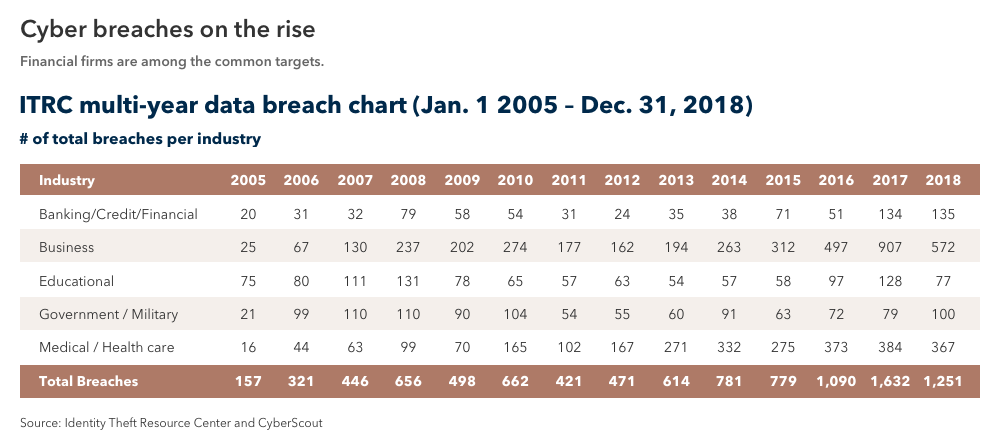
RIA firms, though, aren’t alone in combating the mounting number of sophisticated cyberthreats. Breaches occurred more than 1,250 times at companies and government agencies in 2018, roughly twice the number in 2008, according to the Identity Theft Resource Center and CyberScout. Of those, a tenth of the hacked companies were in the banking, credit or other financial industries.
As the risks heat up, regulators stress that RIAs must play an important role in safeguarding client data. “The federal securities laws require registered investment advisers to adopt written policies and procedures reasonably designed to protect customer records and information,” according to a September 2015 press release from the Securities and Exchange Commission (SEC).
The SEC made this statement while settling charges with an investment adviser firm it alleged “failed to establish the required cybersecurity policies and procedures in advance of a breach that compromised the personally identifiable information (PII) of approximately 100,000 individuals, including thousands of the firm’s clients.”
Locking down computer systems is just one more thing for RIAs to worry about in addition to everything they do for clients. How do you stay ahead of the hackers and work inside of the rules? Edelman offers up three steps for RIAs to follow:
Step 1: Know what regulators require. If there’s good news in all this, it’s that regulators are clear on what’s expected and offer a reasonable set of procedures for RIAs to follow.
Finding out what’s needed is a Web search — or call to the regulator’s office — away. While you should always confirm with legal counsel on cybersecurity requirements, a good place to start is with the SEC’s Office of Compliance Inspections and Examinations (OCIE) checklist. This list shows you in detail what the SEC is expecting RIAs to do with respect to securing systems. This will give you a to-do list of what you need to ask about, Edelman says.
Next, you should consult with the NIST Cybersecurity Practice Guide. This document, which has an executive summary, helps RIA firms understand how digital assets like computers must be secured, how they should be protected and how to document it.
In order to be in compliance, you'll first have to know what is required. Again, check with legal counsel on this. Compliance rules vary based on which regulatory agency you report to, the state you are based in or do business in, and the types of clients you have and how they are regulated. For instance, if you work with pension plans you may need to meet additional requirements. “Figure out what applies,” Edelman says.
Step 2: Comply and get evidence. Don’t simply assume the tech department is “on it” when it comes to cybersecurity. Proving your firm is prepared for cyberthreats isn’t just a quick call to the information technology department and asking “Do we have a firewall?” anymore.
Regulators moved to an “evidence model.” Now, rather than just attesting to regulators, “Yes, we have a firewall,” RIAs must prove it. In this case, you need to produce a photograph of the firewall console screen displayed on the firm’s server, Edelman says. “As you ask for evidence, you gain confidence,” he says.
Most RIA firms satisfy at least part of this requirement by installing so-called cyberauditing software. This software looks over the firm’s computers and devices to make sure the needed protections are in place. The software may verify that devices are adequately locked with multiple passwords and encrypted.
Compliance isn’t merely about installing software. In some cases, it’s about putting procedures in place. You might not only need an Incident Response Plan to describe how you avoid losing data after a cyberattack, but also show that the plan is understood by management and employees.
Here’s some good news. Getting into compliance doesn’t necessarily require spending lots of money. Some of the actions you need are just a matter of turning them on. For example, if you use Windows 10 on computers and tablets, you likely already have device-level encryption available. You need to turn on the BitLocker feature and photograph the BitLocker Drive Encyption screen as evidence. You can find the built-in encryption in the Control Panel under System and Security, and then BitLocker Drive Encryption.
Additionally, there are corporate versions of effective security systems used by consumers. For example, passwords must be secured. If you’re like many, you use services like LastPass to safeguard your own passwords at home. LastPass also provides a corporate-level service, which Edelman says works well for RIAs.
Step 3: Maintain and have documents at the ready. Now that you know what’s expected and can prove it, you need to be ready to quickly show it. This isn’t unique to digital protections. When regulators show up at your office, you should have your compliance manual within easy reach of the chief compliance officer. It’s the same way business continuity planning is handled. Your incident response plan (which outlines the process following a breach) and information security policy (which documents your compliance) should be ready at hand, Edelman says. Make sure it’s a printout, not a file saved on your computer.
The effort needed to comply is worthwhile. Following the protocol can turn regulators into allies if your firm is attacked, Edelman says.
“If you’re in compliance with regulators and you have a breach, the regulators will help you,” Edelman says. “If you’re not in compliance … the regulators are not going to help you. They’re actually going to hurt you. Negligence in cybersecurity is a big deal.”
RELATED INSIGHTS
-
-
Planning & Productivity
-
Insights on Investors
-
Client Relationship & Service
-
Practice Management
-
Portfolio Construction
Use of this website is intended for U.S. residents only.